Have you ever wondered how networks work and what’s really happening on all those wires and network devices?
Networks work by allowing computers and other end devices to share information using an addressing and routing system. This addressing and routing system is self-learning and adaptable with error correction and guaranteed data delivery. Modern networks are designed to be open and flexible.
Modern software that uses networks like the one in your home, office, or the internet typically follows the OSI model. Still, instead of going through that in great detail, I’m going to talk about the basics of how data is transferred and how it traverses the network.
What Are The Basics of Networking?
Modern networks are multiple technologies built up on top of each other in a thoughtful way that enables robust, efficient networking to take place. So what does that mean? Basically, it means that networks are made up of layers. Layers of different technologies working together to solve multiple issues along the path to a great networking solution.
For example, there are all of the electronics that carry the signals, the ability to send messages or data between two devices, and the ability to send messages or data across multiple devices to a far-removed device. All three are very different technical problems to solve, but they all work together to make networking possible.
Electronic systems are inherently dumb. We talk about smart devices all the time, but that usually refers to processing information. In reality, there is no thinking. What smart devices are really good at is trying many things very quickly and failing quickly until the right answer is found.
This is known as iterative problem solving, which is a major strength of modern electronics. Network devices are no different in this regard.
The learning and adaptable features built into modern network technologies are built on top of doing inefficient actions quickly and repeatedly to learn the network and, in turn, capture that information to improve performance in the future. You’ll see what I mean.
What is included in the networking physical layer?
The first layer is the physical layer. This is the layer that includes all of the physical parts of a network. The cable types, their design, and limitations on cable length. It also details cable connector design and the ports that they plug into.
It takes special electronics to manage the data that’s transferred, both on the sending and receiving ends, so that is included. Overall, the first layer is pretty straightforward for many people because it’s easy to visualize the physical components.
If you’re interested in reading more about cable or the cables you may need, you can check out my article on cables..

Something to note is that WIFI, even though it is wireless, is included in the physical layer since it provides the medium that data travels across.
We’ll talk more about the physical devices in a network, but two such critical components include the switch and the router. Both play critical roles in getting your data or data requests to where they need to go.
They can be small devices that sit on your desktop, or in the case of internet service providers, there can be multiple of them in a room that are large appliances mounted into metal racking systems.
I would be remiss if I didn’t talk briefly about the physical equipment used to connect to the internet. The device in question is typically referred to as a modem. Depending on where you live, you may have a DSL modem or digital subscriber link modern, which means internet over copper phone lines.
Another alternative is a cable modem which connects you to the internet over the cable system. Today, a more and more common option is the internet over fiber optics using a fiber modem. This typically delivers the fastest and most reliable speeds but the reliability and speeds available completely depend on your service provider.
What is included in the link layer?
The next layer has a history when it comes to the development of networks that includes a device called a hub. A hub is a network device that connects to your computer with multiple network connections that other hubs or devices can connect to.
When it receives a message on one port, it acts as a repeater, and it broadcasts the message out on all the other ports. It doesn’t store any information, nor does it try to optimize the process. This isn’t a very efficient process and results in a large amount of wasted network capacity due to all the bouncing broadcasts.
Consequently, the hub was replaced by a more efficient device that is commonly used today.
The replacement for the hub is the switch. The switch changes the game by starting as a hub but then tightening things up after the addressing has been sorted out. When the switch receives a message on one of its ports to a new destination, it will check its look-up tables.
If there’s a match, it sends the message to the listed location. If the device confirms there are no matches in its look-up table, the switch broadcasts the message out like a hub would to try and find the receiver. This process is repeated throughout the network until the destination is found.
Once a reply has been received, the switch checks and or makes an entry into one of its look-up tables that includes the destination IP address and the port on the local switch that the data needs to be delivered to get there.
This process creates or updates an entry in the table. Thus, in the future, when a message to that endpoint comes in, the switch knows where to try and forward it first.
But hang on, what about MAC addresses and the communication that takes place between a computer and a switch? This is what we’ve been building towards. This is called the link layer or layer 2. The MAC address is the unique identifier assigned to your network electronics by the factory.
This is used by the switch in a look-up table to keep track of which port has what machine along with which IP address. The link layer also includes the communication protocol or pattern of bits used for communication between a switch and an end device.
The normal IP address type traffic flows on top of this layer, so it’s fundamental to the operation of a network.
The first two layers are so commonly grouped they have a name and are known as Ethernet. If you’re interested in learning more about the first two layers, you can find more details in my article here. Otherwise, let’s move on to the third layer.
What is included in the network layer?
Finally, we made it to the network layer! The third layer is the realm of the IP address and the router. Routers also use look-up tables called routing tables to record the address accessed by forwarding traffic down a given port, but they normally work a little differently.
Often they have an onboard switch. If that’s the case on your router, the switch ports function as a normal switch, but they are connected to the router portion inside. In addition, the router should have its own port meant to connect to other networks outside of your local network called the WAN. Normally this would be the internet.
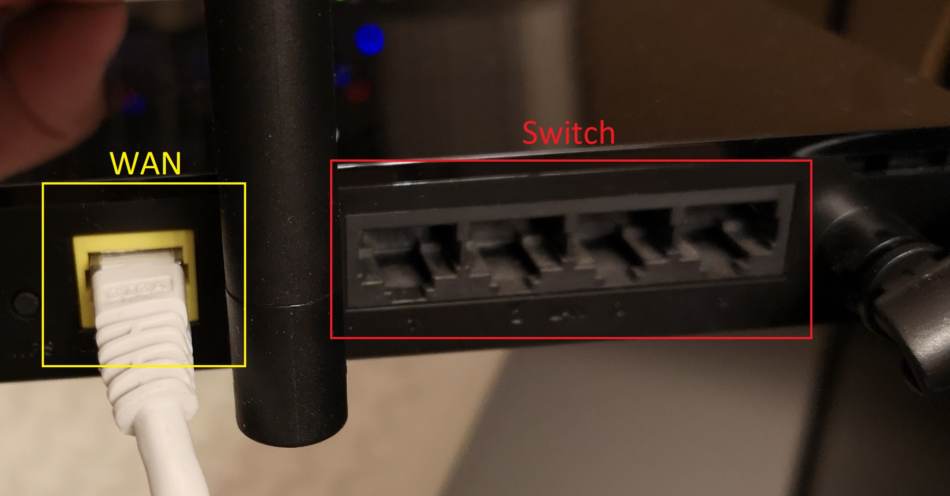
The third layer uses the IP addressing system to send your data from your local network to the local network of someone else. When the destination isn’t on your local switch, the router checks to see if it can find it out in the world of networks known as the internet.
It uses the same kind of broadcast method as the switch until it finds the location. When a reply comes in, the route to the destination is noted in a routing table so that the router knows where to pass your data when you want to access that destination in the future.
Using this process, the router essentially directs traffic across the internet between your computer and anywhere you want to connect to or send data to.
How does a packet of data travel across a network?
Let’s consider the example of what happens when you connect to a computer or device on the network.
When you send or receive data across a network, it gets split into packets. Smaller, more manageable packages of data that the network infrastructure can easily manage. But how do those packets get across the network? They often travel using the TCP/IP protocol, a set of rules or protocols for connecting across a network.
First, when starting a connection, a packet called a SYN or synchronize packet is sent. Your computer sends this packet across the physical link, which includes your cables or WIFI. It rides on top of the link layer that specifies the way your computer talks to the switch so they can understand each other.
Once the switch receives it, the switch checks its local look-up tables for the destination to see if it’s also connected to the switch. If it’s in the list, it forwards the SYN packet to the correct port and waits for a reply. If it isn’t in the list, it broadcasts the SYN packet out all of the switch ports to find it and then waits for a reply.
If one of the ports is a router with access to other networks, it takes charge by finding the destination for the SYN packet outside of the local network. First, it checks its routing tables to see if it already has a route to the destination. If yes, it forwards the SYN packet on the correct route.
If the destination is not in the routing table, the router broadcasts the SYN packet out on the network so the process can repeat over and over until the destination is found. If the network devices can’t find the destination, the connection request will time out in a cascading manner until your computer tells you the connection timed out.
If the network devices can find the destination, an ACK packet for acknowledgment is returned by the destination, which could be a computer or other device. The ACK travels back to the origin, and as it makes its way back, all of the routers and switches adjust their look-up tables to include the route to the destination.
Now, all of these network devices can very quickly send data packets between these two points. When the origin computer receives the ACK, it replies to that packet with a SYN/ACK packet. SYN/ACK is meant to mean synchronize acknowledge.
Once the destination has received the SYN/ACK, a connection between these two points has been established. This connection is what is called a session. The process of sending three messages back and forth between computers is an important feature of TCP/IP and is known as the three-way handshake.
All TCP/IP sessions are established using the three-way handshake process. Thus, it’s an important part of TCP/IP. However, it also plays an important role in developing the look-up tables and routing tables used across the network to operate effectively and efficiently.
Even though I simplified a lot of the process, this is how it works. If you’re interested to know more of the technical detail regarding the TCP/IP protocol and other network standards, you can find them on the IETF website here.
What are the advantages of computer networking?
The advantages of computer networking are plenty.
Computer networking allows for the incredible exchange of information between people that we take for granted today. At any point, you can send a message, and email, or place a call at a moment’s notice to anyone in the world.
Video calls are so good today. It means you can just as easily keep in touch with someone down the block as across the globe. You can download information, engage in entertainment, or get an education.
Today, the internet, the one big network that connects everyone, has provided a platform for entrepreneurs to create information-based products that all of us can access and use to improve our lives.
When people consider the advantages of networking, they often think of all the things they can access over the internet because they see the contributions to their lives. However, the other thing that networking has provided is a reliable and versatile way to connect computers to other devices. An example of this is in industrial settings.
These days, the vendors who create control systems like to use computers to build their main control interfaces. But this presents a problem when connecting to the devices scattered throughout the facility doing all of the heavy lifting control work.
It turns out, using a network is an ideal solution to this problem. High data transfer speeds, high data reliability, and the ease at which you can connect devices make a network an ideal solution.
On the consumer level, the closest we’ve gotten to something like that is a network printer or network storage, but hey, it’s a similar solution to a similar problem. It means you can place your printer or storage almost anywhere instead of needing it to be right beside your computer.
WIFI devices take this even further. In terms of storage, it allows you to rent space on someone else’s computer across the network and store your data there with access similar to having it on your local hard drive.
